Ipset & Trump: Latest News & Developments
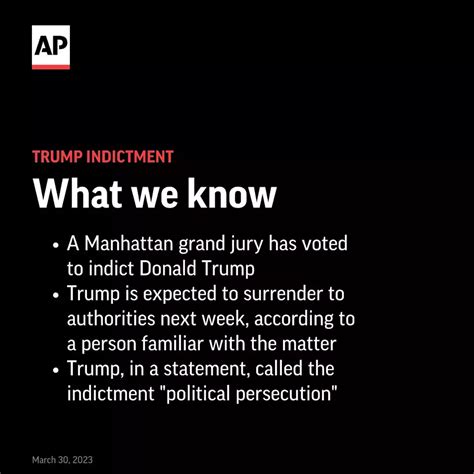
Ipset & Trump: Latest News & Developments
Let’s dive into the whirlwind of
ipset trump news
and developments. In today’s digital landscape, where network security is paramount, understanding the intricacies of tools like
ipset
becomes crucial, especially when interwoven with the ever-evolving political and economic narratives, such as those involving Donald Trump. So, buckle up, guys, as we explore what
ipset
is, how it works, and how it relates to current events.
Table of Contents
What is Ipset?
At its core,
ipset
is a powerful administration tool for Linux that allows you to create and manage IP address sets. Think of it as an advanced way to group multiple IP addresses, networks, or even port numbers under a single name. Instead of creating numerous individual firewall rules, you can create one rule that references an
ipset
. This dramatically simplifies firewall management and improves performance, especially when dealing with a large number of IP addresses. Imagine you need to block access from an entire country or a known list of malicious IPs;
ipset
makes this task much more manageable and efficient.
The real beauty of
ipset
lies in its ability to handle large sets of IP addresses with minimal performance impact. Traditional firewall rules can become sluggish when dealing with thousands or even millions of entries.
ipset
, however, uses indexed data structures, which allow for lightning-fast lookups. This means that your firewall can quickly determine whether an IP address is part of a set without bogging down your system. For network administrators, this is a game-changer, offering a scalable and efficient way to manage network access and security policies.
Furthermore,
ipset
supports various types of sets, including hash:ip, hash:net, and hash:ip,port, each designed for specific use cases. The
hash:ip
type is used for storing individual IP addresses, while
hash:net
is ideal for storing network addresses in CIDR notation (e.g., 192.168.1.0/24). The
hash:ip,port
type allows you to specify both IP addresses and port numbers, providing even more granular control over network traffic. This flexibility makes
ipset
a versatile tool for a wide range of network security applications, from simple IP blocking to complex traffic management scenarios. Whether you’re securing a small home network or managing a large enterprise infrastructure,
ipset
can help you streamline your firewall rules and improve overall network performance.
How Ipset Works
Under the hood,
ipset
works by creating an indexed data structure in the Linux kernel. When you add an IP address or network to an
ipset
, it’s stored in this data structure, which is optimized for fast lookups. When a packet arrives at your firewall, the firewall checks whether the packet’s source or destination IP address is present in the
ipset
. If it is, the firewall can then apply the appropriate rule, such as blocking the packet or allowing it to pass through. The key to
ipset
’s performance is the indexed data structure, which allows the kernel to quickly search for IP addresses without having to iterate through a long list of rules.
To use
ipset
, you first need to create a set using the
ipset create
command. You specify the name of the set, the type of set (e.g.,
hash:ip
), and any options, such as the maximum number of entries the set can hold. Once the set is created, you can add IP addresses or networks to it using the
ipset add
command. You can also remove entries using the
ipset del
command and list the contents of a set using the
ipset list
command. These simple commands provide a powerful interface for managing your IP address sets and controlling network traffic.
Ipset
integrates seamlessly with
iptables
, the standard Linux firewall. You can create
iptables
rules that reference
ipset
sets, allowing you to apply firewall rules to entire sets of IP addresses with a single rule. For example, you can create an
ipset
containing a list of known malicious IP addresses and then create an
iptables
rule that drops all packets originating from those addresses. This approach simplifies firewall management and makes it easier to update your firewall rules as new threats emerge. Furthermore,
ipset
can be used in conjunction with other network security tools, such as intrusion detection systems (IDS) and intrusion prevention systems (IPS), to provide a comprehensive defense against network attacks. By combining
ipset
with these tools, you can create a multi-layered security architecture that is both robust and efficient.
The Trump Connection
Now, where does
ipset trump news
fit into all of this? Well, Donald Trump’s policies and actions, particularly in the realm of international relations and trade, have often led to significant shifts in network traffic patterns and security concerns. For instance, trade disputes with China or sanctions against certain countries can result in the need to block or filter traffic from specific IP address ranges associated with those regions. In such scenarios,
ipset
becomes an invaluable tool for network administrators tasked with implementing these policies.
Consider a hypothetical situation where the U.S. government imposes sanctions on a particular country, and one aspect of these sanctions involves blocking access to certain online services from that country. Network administrators responsible for these services could use
ipset
to create a set containing the IP address ranges associated with that country and then configure their firewalls to block traffic from those IPs. This ensures compliance with the sanctions and prevents users in the sanctioned country from accessing the services. The efficiency and scalability of
ipset
make it well-suited for this type of task, allowing administrators to quickly and effectively implement the necessary restrictions.
Moreover, the political climate surrounding Trump’s administration has often been characterized by heightened cybersecurity threats. Whether it’s concerns about foreign interference in elections or the risk of cyberattacks on critical infrastructure, network security professionals have had to be vigilant in protecting their systems.
Ipset
can play a crucial role in these efforts by providing a flexible and efficient way to block malicious traffic and mitigate potential threats. For example, if a network administrator detects a surge of suspicious traffic originating from a particular IP address range, they can quickly add those IPs to an
ipset
and block them at the firewall, preventing the traffic from reaching their servers. This proactive approach to network security can help organizations stay ahead of potential attacks and protect their valuable data. In this context, the intersection of
ipset
, network security, and political events highlights the importance of understanding and utilizing these tools to safeguard against evolving threats.
Real-World Use Cases
To illustrate the practical applications of
ipset
, let’s explore a few real-world scenarios:
Blocking Malicious IPs
One common use case is blocking known malicious IP addresses. Security organizations and threat intelligence providers often maintain lists of IPs associated with botnets, malware distribution, and other malicious activities. You can use
ipset
to create a set containing these IPs and then configure your firewall to block all traffic from those addresses. This helps protect your network from a wide range of threats, including malware infections, denial-of-service attacks, and brute-force attacks.
To implement this, you would first obtain a list of malicious IPs from a reputable source. Then, you would create an
ipset
of type
hash:ip
and add the IPs to the set. Finally, you would create an
iptables
rule that drops all packets originating from the IPs in the
ipset
. This simple setup can significantly enhance your network security posture and reduce the risk of successful attacks. Regularly updating the list of malicious IPs in the
ipset
is crucial to ensure that you are protected against the latest threats. This can be automated using scripts that periodically download updated lists and update the
ipset
accordingly.
Geoblocking
Another popular use case is geoblocking, which involves blocking traffic from specific countries or regions. This can be useful for preventing attacks from countries known for harboring cybercriminals or for complying with legal restrictions that prohibit access to certain content from specific regions.
Ipset
makes geoblocking relatively straightforward. You can find lists of IP address ranges associated with different countries and then create an
ipset
containing those ranges. Finally, you can configure your firewall to block traffic from the IPs in the
ipset
.
The key to effective geoblocking is obtaining accurate and up-to-date lists of IP address ranges for each country. Several online resources provide this information, but it’s important to verify the accuracy of the data before using it. Once you have the lists, you can create an
ipset
of type
hash:net
and add the IP address ranges to the set. Then, you can create an
iptables
rule that drops all packets originating from the IPs in the
ipset
. Geoblocking can be a powerful tool for reducing the attack surface of your network and protecting against region-specific threats. However, it’s important to consider the potential impact on legitimate users who may be located in the blocked regions.
Traffic Shaping
Ipset
can also be used for traffic shaping, which involves prioritizing or limiting traffic based on its source or destination. For example, you might want to prioritize traffic from your internal network over traffic from the internet or limit the bandwidth available to certain users or applications.
Ipset
can help you identify the traffic you want to shape by grouping IP addresses or networks into sets. You can then use
iptables
and other traffic shaping tools to apply the appropriate policies to the traffic in those sets.
To implement traffic shaping with
ipset
, you would first identify the IP addresses or networks that you want to prioritize or limit. Then, you would create an
ipset
of the appropriate type (e.g.,
hash:ip
or
hash:net
) and add the IPs or networks to the set. Finally, you would use
iptables
and other traffic shaping tools, such as
tc
(traffic control), to apply the desired policies to the traffic in the
ipset
. For example, you could use
tc
to create a queueing discipline that limits the bandwidth available to the traffic in the
ipset
. Traffic shaping can help you optimize network performance and ensure that critical applications receive the resources they need.
Conclusion
In conclusion,
ipset
is a versatile and powerful tool for managing IP address sets and enhancing network security. Its ability to efficiently handle large sets of IP addresses makes it invaluable for a wide range of applications, from blocking malicious IPs to implementing geoblocking and traffic shaping. While the connection to
ipset trump news
might seem tangential, the reality is that political and economic events often have a direct impact on network traffic patterns and security concerns. Understanding tools like
ipset
is therefore essential for network administrators and security professionals who need to adapt to these changing circumstances and protect their networks from evolving threats. So keep your
ipset
skills sharp, guys, and stay informed about the latest developments in both technology and world events!